While remote access to machines gains popularity, it’s time to talk about cybersecurity in manufacturing and bridging the IT/OT security gap.
COVID drove home the need for remote access to machines, lines, and equipment at the enterprise level, whether for systems integrators, operators, vendors, analysts, or other employees. Even in a fully automated factory, robots can’t do it all.
As a motion control leader, Mitsubishi Electric knows connected automation systems, as well as the human resourcefulness required to keep those systems running smoothly and efficiently. We’ve been helping manufacturing businesses adapt and evolve with remote access technologies — PLCs, HMIs, collaborative robots, control networks, and more — since well before the first COVID lockdowns.
But cyber attackers are constantly upping their game too. Because any network, device, or endpoint can be a potential mark for hackers, we believe that when it comes to cybersecurity, there’s no such thing as “overprotective.”
Partners in Cyber-Crime Prevention
That’s why Mitsubishi Electric formed an e-F@ctory Alliance partnership with Dispel to improve the cybersecurity resilience and operational efficiency of our customers and partners. Dispel is the world’s leading provider of industrial control system (ICS) zero trust network access that utilizes both zero trust and moving target defense.
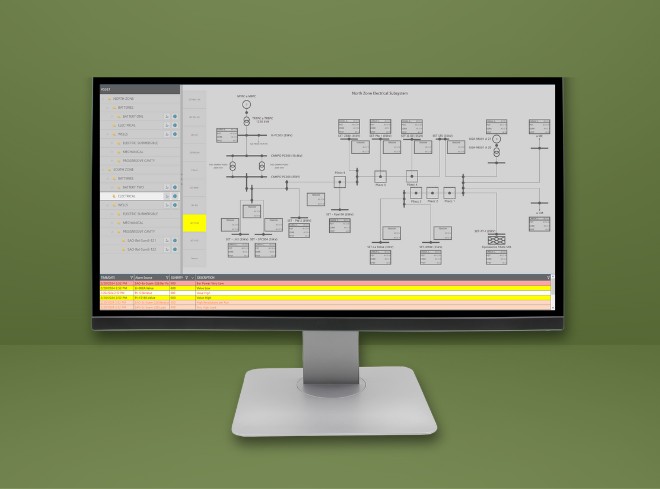
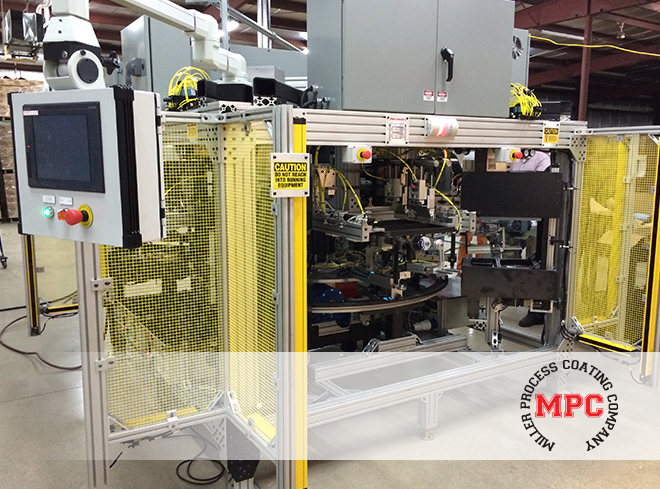
It’s all about getting operators and third parties to systems quickly and securely. Dispel’s certified plug-and-play deployment with Mitsubishi Electric hardware, such as our iQ-R PLC rack, gives you easy access to every device in your facility with one install and lets you use your equipment as the uplink gateway. The result is secure two-way communication that bridges the gap between information technology (IT) and operational technology (OT) capabilities. Remote users can control and monitor facilities from any approved location via a well-defended pathway.
Sessions are screen recorded for troubleshooting, auditing, and in the case of attempted foul play, evidence-based purposes. You can even attach a webcam or other components to literally see what’s happening on the factory floor.
Less Static = More Secure
IT/OT coordination isn’t all that sets our solution apart. Typical remote access security applications employ a static defense. This all-or-nothing strategy protects assets by building barriers around them — DMZs, VPNs, firewalls, and the like. But static defenses allow potential attackers to study your systems extensively and pick the time and place for a breach.
Dispel combines several cutting-edge approaches that make it the first and only remote access platform to align with the most recent of the National Institute of Standards and Technology’s (NIST’s) stringent cybersecurity guidelines. The NIST framework includes NIST CSF, 800-53, 800-82, 800-160 Vol. 2 for cyber resiliency, and the draft revision of NIST CSF 2.0.
Zero Trust
Dispel’s zero trust approach ensures that access to your network is only granted to the right people at the right time. All potential users must put in a request to an administrator or owner and pass a detailed approval process.
Users must verify that they match all criteria at the assigned time before they can make the initial connection, which is only provided for specified ports on a single device, with additional devices available to be added at the customer’s discretion. Each day, the user is given a fresh, secured environment in which to operate. Once the work concludes, the segmented environment is destroyed.
Moving Target
Because authorized access is only the first step in cybersecurity, Dispel’s moving target defense is leading-edge. Each time an authorized user connects to the network, the pathway is unique and varied across multiple cloud servers. Every new session will result in a completely different pathway.
Think of it in terms of a mail truck that takes the same delivery route every day. It would be very easy for someone to monitor that truck’s likeness and daily driving path in order to steal their intended target’s mail.
Now, imagine that same mail truck is able to change its likeness daily and take a different route each day to deliver the mail. This is moving target defense, which makes it very difficult for someone to learn the pathway from a remote PC to the customer’s facility.
Dispel uses multiple general cloud spaces, like Amazon and Azure, to conceal your identity amongst all the other traffic. If a hacker gains knowledge of the first cloud, the next pathway will be completely different, and the next, and the next…
Virtual Sandbox
What’s more, remote access users don’t actually connect to your facility. Instead, they connect to a segmented virtual machine that is hardened to the U.S. Defense Information Systems Agency’s security standards. Access is provided to one specific user to perform one specific task on one specific software.
Like sands through an hourglass, once the user saves the program to the virtual desktop and closes out, the connection is gone. Even if someone tries to plant something nefarious, the next user will boot up to a fresh environment. The malicious implant will be sandboxed and destroyed in a controlled manner, preventing any further access by the attacker.
As Seen at the Gartner Show
Mitsubishi Electric recently joined Dispel at the Gartner Security & Risk Conference in National Harbor, MD, to provide a demonstration. The event is a “who’s who” for all types of security solutions — remote access, risk mitigation, network traffic filtering, and more.
We were the ONLY factory automation exhibitor to showcase OT capabilities, and we’re proud to be at the forefront of this crucial technology. Our “ASSISTA Says” demonstration incorporated a Mitsubishi Electric PLC, HMI, and ASSISTA collaborative robot to illustrate remote monitoring and control.
Many booth visitors said they were glad to see a focus on OT remote access – as that had been a concern for them at their facilities – while playing the demo which mimics one of the original electronic games of many of our childhoods, Simon Says. They expressed how convenient it would be to incorporate an ICS solution without needing to make any major modifications to their ICS environment.
Try it Yourself
Mitsubishi Electric and Dispel will again demo our ICS cybersecurity solution at future shows, starting with the Black Hat conference in August. If you can’t come and try our demo there, talk to one of our engineers about a solution for your organization at https://go.meau.com/contactsales.
Work with Us and Succeed
We love our customers and the challenges they bring to us. We also like to let our customers shine by discussing how we worked together to solve their biggest challenges. If you have a challenge that needs to be solved and would like to be our next BIG success story, reach out to us and let’s connect!